Enhance your Kubernetes cluster management on Microsoft Azure with KRS (Kubetools Recommender System) – a new powerful tool designed to provide recommendations and health checks using AI. KRS scans your cluster to identify deployed pods, services, and deployments, analyzes the tools used, and provides rankings based on their popularity. With features like generating recommendations, performing health checks, and exporting pod information, KRS supports both OpenAI and Hugging Face models to ensure your Kubernetes environment runs efficiently. This guide will walk you through setting up KRS for an EKS cluster on Azure, from installation to advanced usage.
Prerequisites:
- An Azure account
- Install Azure CLI on your laptop
Installation of KRS:
1. Clone the repository using the command
git clone https://github.com/kubetoolsca/krs.git
Install the Krs Tool:
Change the directory to /krs and run the following command to install krs locally on your system:
pip install .
Check if the tool has been successfully installed using:
krs --help
Once you get a list of commands you can move on to the next part.
Create an EKS cluster on your Azure account:
To create an EKS account, you can log into your account and search for Azure Kubernetes Service.
Once you click create, you can name your cluster, add a node pool (I used the default agent pool but you can create your own), and leave everything else to its default state. This will help you create a cluster.
Install Azure CLI:
To install the CLI, I used the command-
brew update
brew install azure-cli
Log into your Azure account
Once the CLI is installed, log into your Azure account using the command:
az login
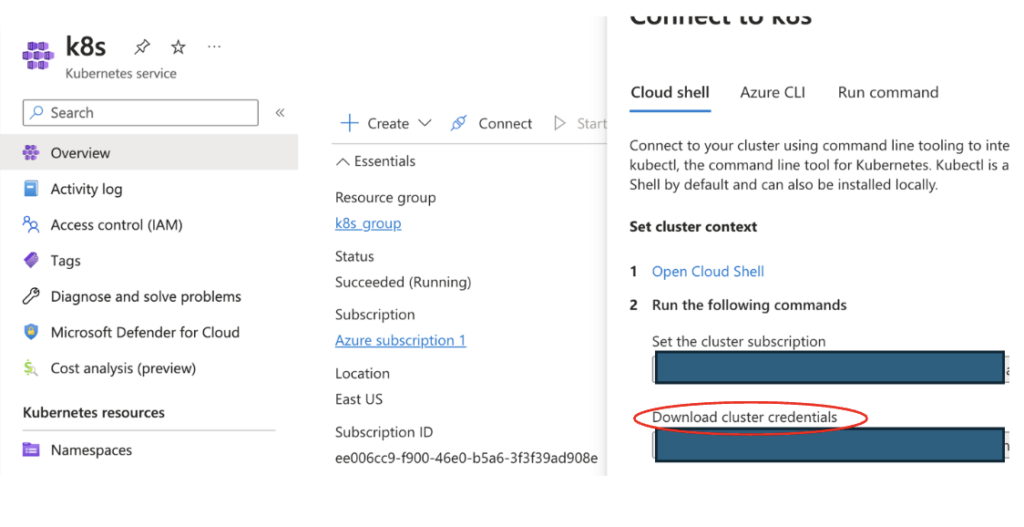
Connect to Your Cluster:
Retrieve the connection command from your cluster details on the Azure portal and execute it to connect to your cluster.
Using Krs
Initialise Krs:
% krs init
Scan the Clusters:
% krs scan
Scanning your cluster...
Cluster scanned successfully...
Extracted tools used in cluster...
The cluster is using the following tools:
+-------------+--------+-----------------------------+---------------+
| Tool Name | Rank | Category | CNCF Status |
+=============+========+=============================+===============+
| autoscaler | 5 | Cluster with Core CLI tools | unlisted |
+-------------+--------+-----------------------------+---------------+
Get Recommended Tools:
% krs recommend
Our recommended tools for this deployment are:
+-----------------------------+------------------+-------------+---------------+
| Category | Recommendation | Tool Name | CNCF Status |
+=============================+==================+=============+===============+
| Cluster with Core CLI tools | Recommended tool | k9s | unlisted |
+-----------------------------+------------------+-------------+---------------+
Install Helm
brew install helm
Install Kubeview
helm install kubeview kubeview
NAME: kubeview
LAST DEPLOYED: Sat Jun 29 21:44:17 2024
NAMESPACE: default
STATUS: deployed
REVISION: 1
NOTES:
=====================================
==== KubeView has been deployed! ====
=====================================
To get the external IP of your application, run the following:
export SERVICE_IP=$(kubectl get svc --namespace default kubeview -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
echo http://$SERVICE_IP
NOTE: It may take a few minutes for the LoadBalancer IP to be available.
You can watch the status of by running 'kubectl get --namespace default svc -w kubeview'
Scan the cluster
krs scan
Scanning your cluster...
Cluster scanned successfully...
Extracted tools used in cluster...
The cluster is using the following tools:
+-------------+--------+-----------------------------+---------------+
| Tool Name | Rank | Category | CNCF Status |
+=============+========+=============================+===============+
| kubeview | 30 | Cluster with Core CLI tools | unlisted |
+-------------+--------+-----------------------------+---------------+
| | 3 | Cluster Management | unlisted |
+-------------+--------+-----------------------------+---------------+
| autoscaler | 5 | Cluster with Core CLI tools | unlisted |
+-------------+--------+-----------------------------+---------------+
Export pod info with logs and events
% krs export
Pod info with logs and events exported. Json file saved to current directory!
meetsimarkaur@meetsimars-MBP krs % ls
CODE_OF_CONDUCT.md arch.png gke.md kubeview
CONTRIBUTIONS.md bhive.png krs samples
LICENSE build krs.egg-info setup.py
README.md exported_pod_info.json kubetail
Detect and Fix Issues with the cluster
% krs health
Starting interactive terminal...
Choose the model provider for healthcheck:
[1] OpenAI
[2] Huggingface
>> 1
Installing necessary libraries..........
openai is already installed.
Enter your OpenAI API key: sk-proj-xxxxxxx
Enter the OpenAI model name: gpt-3.5-turbo
API key and model are valid.
Namespaces in the cluster:
1. default
2. kube-node-lease
3. kube-public
4. kube-system
Which namespace do you want to check the health for? Select a namespace by entering its number: >> 1
Pods in the namespace default:
1. kubeview-64fd5d8b8c-khv8v
Which pod from default do you want to check the health for? Select a pod by entering its number: >> 1
Checking status of the pod...
Extracting logs and events from the pod...
Logs and events from the pod extracted successfully!
Interactive session started. Type 'end chat' to exit from the session!
>> Everything looks good!
Since the log entries provided are empty, there are no warnings or errors to analyze or address. If there were actual log entries to review, common steps to resolve potential issues in a Kubernetes environment could include:
1. Checking the configuration files for any errors or inconsistencies.
2. Verifying that all necessary resources (e.g. pods, services, deployments) are running as expected.
3. Monitoring the cluster for any performance issues or resource constraints.
4. Troubleshooting any networking problems that may be impacting connectivity.
5. Updating Kubernetes components or applying patches as needed to ensure system stability and security.
6. Checking logs of specific pods or services for more detailed error messages to pinpoint the root cause of any issues.
>> 2
>> Since the log entries are still empty, the response remains the same: Everything looks good! If you encounter any specific issues or errors in the future, feel free to provide the logs for further analysis and troubleshooting.
>> end chat
Using KRS, you can effortlessly identify and optimize the tools within your Kubernetes clusters, whether on-premises or in the public cloud. The krs command feature, in particular, stands out by suggesting tools that are better suited for your cluster’s specific needs. Discovering this functionality was a revelation, showcasing the tool’s ingenuity in enhancing cluster management. It’s a testament to the advanced capabilities of KRS, making it an indispensable asset for SRE and DevOps engineers and teams.




